In the past, there were no regulations governing automotive cybersecurity at the organizational level. An automotive original equipment manufacturer (OEM) could claim that the vehicle was secured against cyberattacks and then silently rework attack paths discovered by ethical hackers.
In 2020, the United Nations Economic Commission for Europe (UNECE), the United Nations (UN) harmonization body for vehicle type approvals in Europe, published regulations requiring vehicle manufacturers to establish a management system for cybersecurity and software updates, which must be confirmed and certified by independent third parties to meet the requirements of domestic registration authorities. European Union (EU) member countries, Japan and South Korea apply these regulations to most road vehicles.
The UNECE regulations require coordinated cybersecurity activities at the organizational level (which is different from project-level cybersecurity measures, such as encryption). Organizational-level requirements encompass processes, responsibilities and measures —necessary to establish the security of the connected vehicle. These requirements may necessitate significant changes to manufacturers’ and suppliers’ research and development (R&D) activities and other areas throughout the organization.
For example, threat analysis and risk assessment (TARA) is a structured procedure for systematically identifying and assessing risks. Risk assessments must be carried out on a regular basis — even when the vehicles are already on the road.
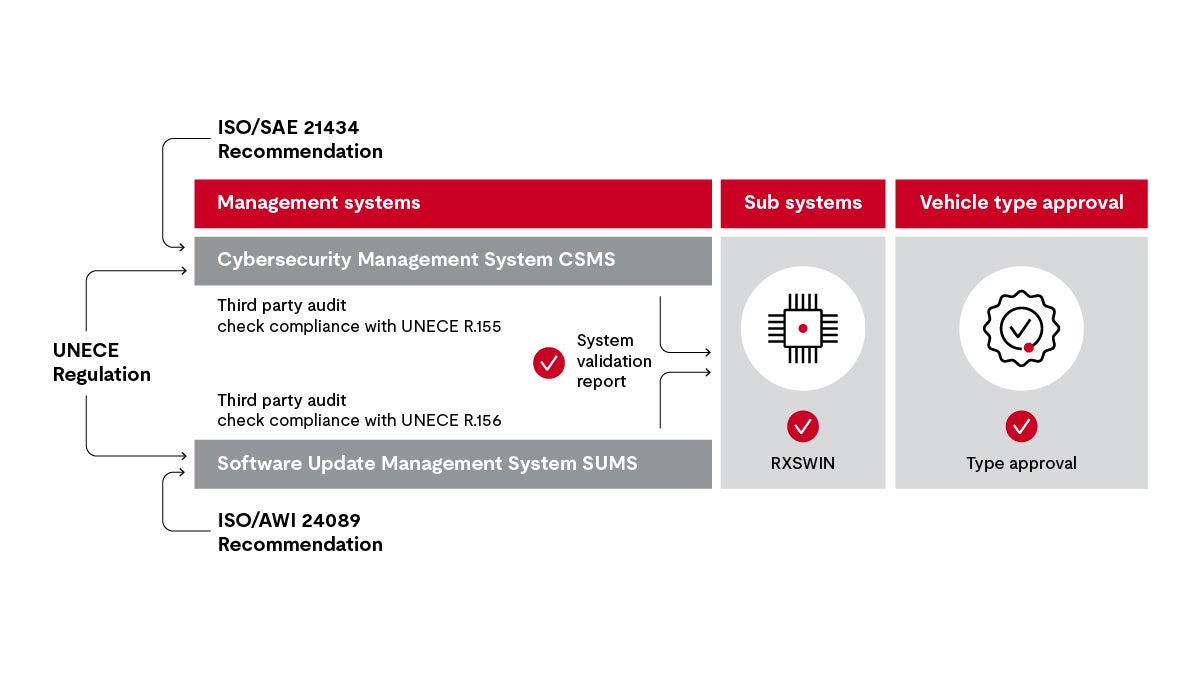
The diagram below shows the main characteristics of the UNECE regulations.

As shown on the left side of the diagram, there are two UNECE regulations with similar requirements: UN R155, which specifies requirements for a cybersecurity management system (CSMS), and UN R156, which specifies requirements for the software update management system (SUMS).
Cybersecurity management system
Cybersecurity extends far beyond encryption of a system. The OEM must set up a cybersecurity management system (CSMS) that covers the entire vehicle life cycle in compliance with ISO/SAE 21434. This includes:
- Development
- Production
- Operation
- Scrapping
The CSMS is particularly important for vehicle scrapping due to privacy concerns, as connected vehicles contain a large amount of personal data.
After you set up your CSMS, an independent auditor must check the management system for compliance with UN R155 requirements, including whether a TARA is conducted regularly and whether cybersecurity concept goals feed into product development. If you meet all applicable requirements, you will receive a certificate.
Software update management system
Software updates are crucial to keeping a connected vehicle secure throughout its lifecycle. ISO 24089 specifies requirements and recommendations for road vehicle update engineering at the organization and project level. You must establish a software update management system (SUMS), which also must be audited to the UN R156. The auditor checks whether the SUMS processes meet the objectives. If the SUMS meets requirements, you will also receive a certificate, which is valid for three years.
An important component of SUMS processes is how the Regulation Software Identification Number (RXSWIN) is assigned and managed. RXSWINs are part of a software identification scheme and are assigned for each component. The RXSWIN helps the manufacturer keep track of the current software configuration of a vehicle system.
In addition to the OEM’s management system, its technical software update systems — the software handlers in back-end systems and on the vehicle side — must be approved. Declarations of conformity for the SUMS and CSMS are a precondition for all type approvals of the vehicle's subsystems.
Vehicle type approval
An independent auditor must check the CSMS, SUMS and all software update systems within and outside the vehicle. When your development team has completed the system, the independent auditor checks the release candidate together with the compliance statements for the systems.
Then the system is submitted to the national registration authority. This agency expects certificates from the manufacturer for the CSMS, software update system validation and RXSWIN.
Once the manufacturer receives all system approvals, they receive a type approval for the vehicle, which is required before a vehicle is allowed to be sold in a particular country.
A CSMS can help you establish that all necessary cybersecurity activities before, during and after product development are carried out diligently until the last vehicle is due for scrapping.
Cybersecurity must not be an afterthought; rather, it must be considered from the very beginning and maintained throughout the life cycle. Software updates are critical to the connected vehicle's security throughout its life cycle.
Watch our video to learn more about UNECE compliance requirements.
Get connected with our team
Thanks for your interest in our products and services. Let's collect some information so we can connect you with the right person.
