To learn more about this topic, register for our automotive cybersecurity training sessions.
In the past, there were no regulations governing automotive cybersecurity at the organizational level. An automotive original equipment manufacturer (OEM) could claim that a vehicle was secured against cyberattacks but silently continue to make security updates after the vehicle was purchased,
Threat analysis and risk assessment (TARA) is a structured procedure for systematically identifying and assessing risks. Risk assessments must be carried out on a regular basis — even when the vehicles are already on the road.
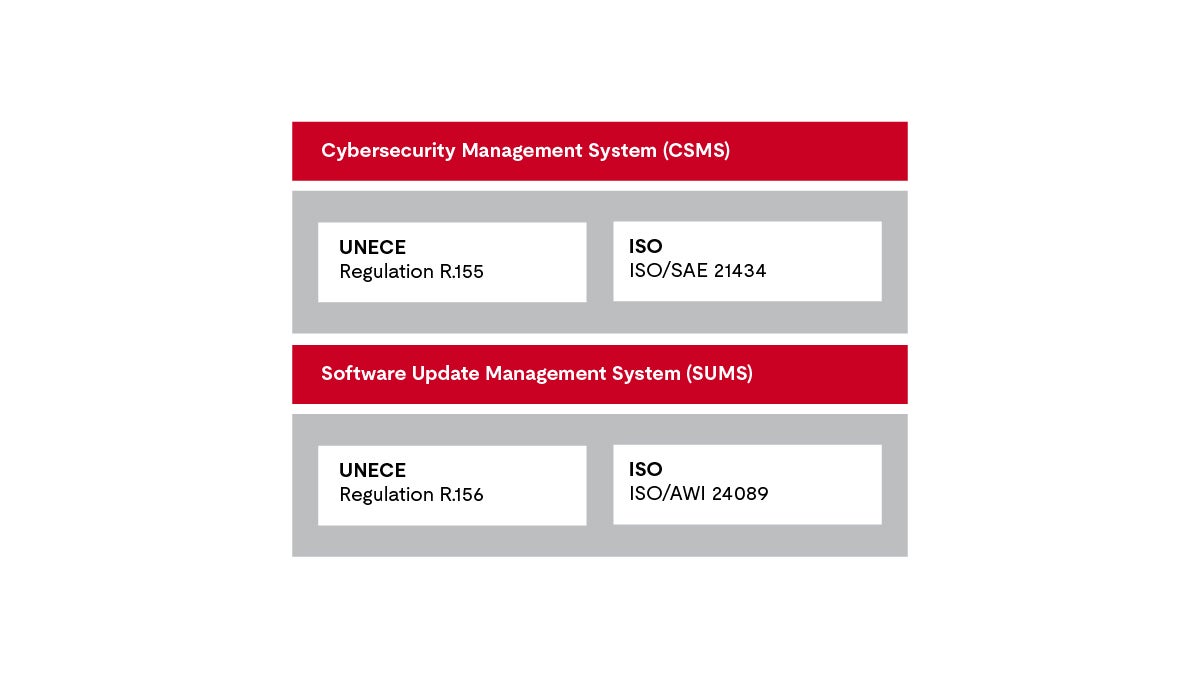
The UNECE World Forum for Harmonization of Vehicle Regulations (WP.29) is the United Nations harmonization body for vehicle type approvals in Europe. In the summer of 2020, WP.29 resolved that vehicle manufacturers would be required to have a management system for both cybersecurity and software updates. Independent third parties must check and confirm the validity of these systems. The domestic registration authorities for vehicles expect this certification. The EU countries, as well as Japan and South Korea, have decided to apply these UNECE regulations to most road vehicles.

Cybersecurity at organizational level requires:
- Defined processes
- Responsibilities
- Measures
In other words, cybersecurity must specify who does what and when, so that the connected car remains secure.
Cybersecurity management systems (CSMS)
Fortunately, we have guidance for this task. ISO/SAE 21434 provides valuable information on how to set up a CSMS.
In addition to the project phase in product development, there is also:
- Production.
- The operating phase by the buyer.
- The scrapping of the vehicle.
This third phase is particularly sensitive for privacy reasons, because a connected car that’s been scrapped could contain a large amount of personal data. Cybersecurity is much more than just the encryption of a system. It affects almost everything you do.
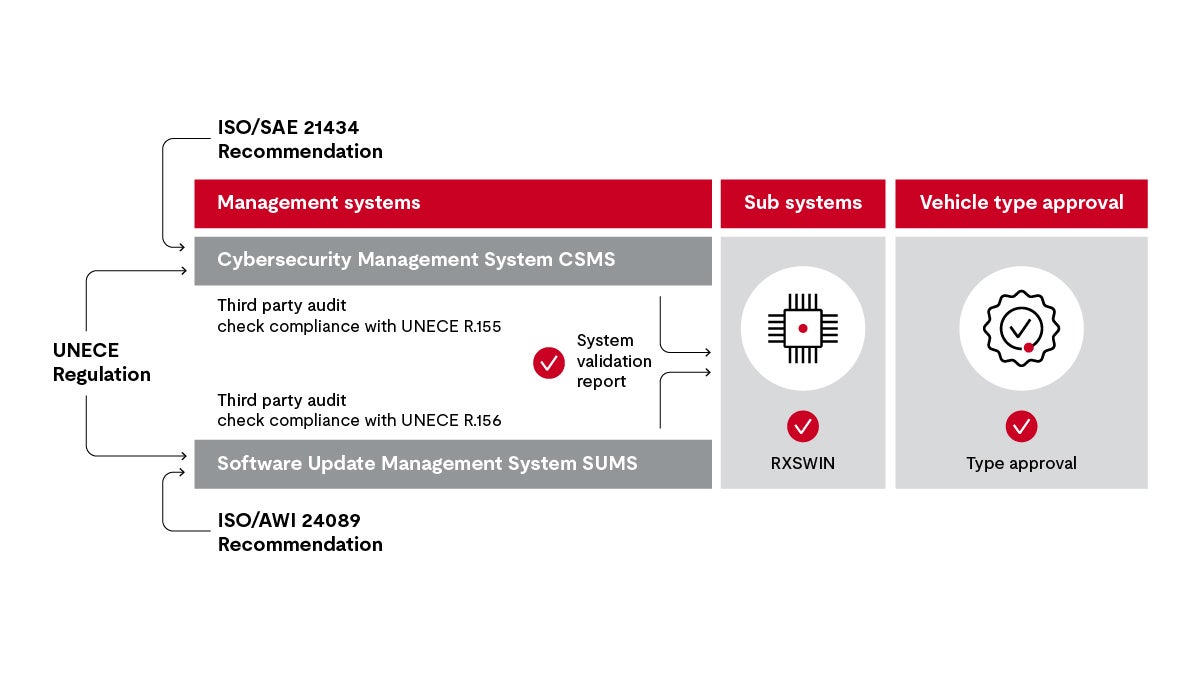
When you are finished with your CSMS, an independent auditor comes to your site to check whether the management system complies with the requirements resulting from the UNECE regulation. For example, is TARA conducted regularly, or do the goals from the cybersecurity concept feed into product development?
The basis for the audit will be the UNECE Regulation R155.
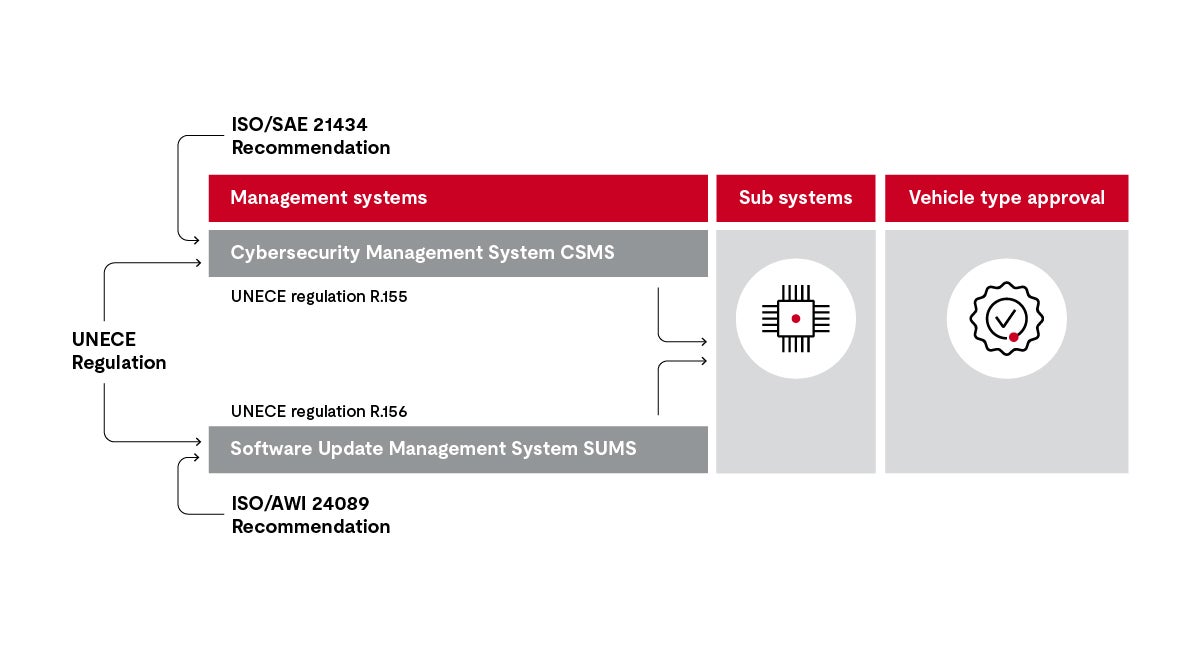
Software Update management systems
The software update management system can be guided by ISO AWI 24089, for example. The first step corresponds to the procedure for CSMS: The auditor checks whether the processes of the software update management system meet the objectives.
Software updates are ultimately the key to keeping the connected car permanently secure. If everything fits, you will also receive a certificate for the Software Update Management System SUMS, which is valid for three years. An important component of the SUMS is the process by which the RX Software Identification Numbers (RXSWINs) are assigned and managed. The manufacturer has to keep an account of this activity and set up a register. RXSWINs are part of a software identification scheme and are assigned for each component that is considered to be security-critical. With RXSWINs, the manufacturer always knows the current software configuration of a vehicle system. In addition to the car manufacturer’s management system, its technical software update systems must also be approved, the SW handlers both on the back-end systems and on the vehicle side. Both Software Update Management System and SW Update System declarations of conformity are a precondition for all type approvals of the vehicle’s subsystems.
If we merge both strands, we have three systems that an independent auditor must confirm: a cCSMS, a software update management system and all software update systems, both within and outside the vehicle.
As you have certainly seen by now, in cybersecurity, project concerns and the organization’s backup go hand in hand. You call the independent auditor again when your development team has completed development. They check the release candidate together with the compliance statements for the management and update systems.
Vehicle type approval
Now it goes to your national registration authority. This agency expects numerous certificates from the manufacturer regarding the CSMS and the system validation report from the software update strand. And of course, the RXSWIN of your system.
Based on all system approvals, the manufacturer finally receives a type approval for the vehicle.
With your CSMS, you establish that all necessary cybersecurity activities before, during and after product development are carried out diligently, until the last vehicle is due for scrapping. Cybersecurity is not an afterthought. Rather, it has to be considered from the very beginning and maintained throughout the lifecycle. That’s why software updates are so important to maintain the security of the connected vehicle.
About the author
Thomas Liedtke is a computer scientist by background. After completing his PhD at the University of Stuttgart, he entered the telecommunications industry. Over the course of 14 years at Alcatel-Lucent, he successfully spearheaded a variety of projects and managed several departments. He entered the field of consulting over a decade ago and has been sharing his experience with clients in a variety of industries ever since, primarily in the areas of safety, security, privacy and project management.
He has been involved with several committees, particularly the working group for Automotive Cybersecurity at German Electrical and the VDA Cybersecurity Work Group.
