What makes a management system for cybersecurity so important?
There is an invisible expiration date on cybersecurity. Encryption is a good example of this; a key that cannot be broken today may not even be an obstacle tomorrow. Then attackers will develop better tools and additional know-how, so cybersecurity is a moving target.
Let’s start with a hypothetical scenario of what these two requirements mean in practice. Based on that, we’ll work out three key challenges that every vendor in the automotive industry is confronted with. After this, we’ll see which elements you can use to set up your cybersecurity management system.
The scenario
Imagine this critical and urgent situation. A vendor, Shǎndiàn, is a car maker from Pagaan. Shǎndiàn is responsible for monitoring the security posture of his fleet of cars. The security operation center detects an attack is beginning: An initial event analysis using a field-return car shows that the attack compromises a control unit developed by Delta Components, one of the leading system suppliers. This hack may lead to the theft of some personal data. The range analysis shows that only a small portion of the fleet in Asia will be affected, as the attack can’t be scaled to other vehicle types or regions. How could Shǎndiàn react to cope with the risk?
With this scenario in mind, we’ll explain three challenges of a Cybersecurity Management System.
1. Challenge: Quick but safe and secure response
A fast response relies on good forensics. Delta Components, the supplier responsible for the compromised control unit, has a well-trained analytics and incident response team. After a few days, the team understands the situation. They inform Shǎndiàn’s incidence response unit that they don’t recommend developing a patch at the moment. A couple of days later, Shǎndiàn agrees to accept the risk for the time being. The vulnerability will be locked with the next regular functional update.
Why did Shǎndiàn decide to accept the risk? Because an intermediate solution to stop the attack would limit the cars’ functionality. A risk assessment would have determined the risk value and evaluated the severity of the damage: functional, financial, operational and privacy. None of these categories indicated enough of an impact to require immediate action.
The decision to accept the risk is a serious balancing act: Shǎndiàn had a tradeoff to make between the risk and the users’ inconvenience.
Aside from the responsibilities of the incident response team and the vulnerability test team, dedicated effort is required to understand what other products may have the same vulnerability, and which lifecycle phase those products are in.
Finally, a dedicated communication plan needs to be prepared by both Shǎndiàn and Delta Components. The purpose is to make sure that all relevant partners — customers, road users, regulatory bodies and others — get the information they need through appropriate channels.
To summarize, a quick response essentially builds on these CSMS elements:
- Collection of relevant cybersecurity information
- Triage-collected cybersecurity information using triggers.
- Assessment of cybersecurity events.
- Identification and analysis of cybersecurity vulnerabilities.
- Management of identified cybersecurity vulnerabilities, if applicable.
2. Challenge: Maintaining cybersecurity over the lifecycle
Companies need to maintain security over a lifetime. Let’s add another detail to the above scenario: Imagine the vulnerability became public in a hacker conference a half year earlier. Why might Delta Components not have responded then? Well, you must become aware of vulnerability before you can act on it. A Tier 1 of a certain size and legacy has literally hundreds of thousands of products and variants of products at various relevant stages of the lifecycle. Combine this with the number of potential vulnerabilities, and we can easily see that the sheer number of risks is overwhelming. No organization can manage this by hand.
Therefore, a key aspect of a CSMS is to build an infrastructure with dedicated tools that automate these types of tasks. Scanning databases for new vulnerabilities and checking whether existing products could be affected is a task that should be performed routinely. This can be done internally or with the help of a partner. In addition, information about security vulnerabilities can come from other sources. These may be newsletters, conferences, partners, suppliers, industry working groups, bug bounty parties — and even information from the darknet. Therefore, a process must be in place to ensure that the organization regularly scans relevant sources, separates noise from relevant information and analyzes information about potential vulnerabilities to understand if the risk landscape has changed.
Without effective monitoring mechanisms, Delta Components cannot keep cybersecurity up to date. In summary, maintaining cybersecurity over the lifecycle is essentially built on these CSMS elements:
- Strategy to scan products and their parts for vulnerabilities throughout the lifecycle.
- Structured approach to scanning external sources of information about weaknesses and vulnerabilities.
- Criteria for filtering out noise from relevant information (the “triage”).
- List of all vulnerabilities and associated information, and analysis about which of them are managed and which are critical.
- Continuous monitoring that controls are still effective.
- Keeping the risk assessments current regarding attacks, vulnerabilities, etc.
- Continuous maintenance of the asset databases to anticipate support for event assessments.
3. Challenge: How to make your CSMS effective
The third challenge for companies is to integrate cybersecurity work with our work streams. Let’s take a short look at what makes a cybersecurity management system effective. Your company already has management systems for quality, risk management, work safety, environmental management and so on.
How can you integrate CSMS requirements into this already existing process landscape?
This is easier said than done. After all, in an organization there are real people with their own interests. Integration is most likely to succeed when it results in a well-structured management system that works well with each of these various goals. This regulates at which level and in which area of the company particular subsystems come into play. As an example: The requirements for product development are, in fact, different from those for production. Accordingly, the subsystems are based on different industry standards. With the integrated management system, you govern each issue at the appropriate level. By interlinking them, you ensure that cybersecurity and other management issues will be part of day-to-day business without question.
How to design a CSMS
Now you have learned why a cybersecurity management system matters. Let’s get to the next step: How can you design a CSMS to benefit your company?
As you already know, you must ensure that:
- Your products are designed to be secure over a lifetime.
- New information on vulnerabilities is constantly being evaluated.
- This information is acted upon accordingly.
These tasks require ongoing efforts at both the enterprise and operation levels. To thoroughly coordinate these activities, regulators expect a CSMS.
Incorporate the CSMS into your leading management system. That way, you seek out and address cybersecurity concerns along with other lifecycle requirements. Carefully define when your staff needs to refer to the appropriate subsystem. Then they will take care of the right concern at the right time. Let's look at how you can integrate your concerns into a higher-level management system.
According to the definition presented in UNECE regulation R.155, a “CSMS means a systematic risk-based approach defining organizational processes, responsibilities and governance to treat risk associated with cyber threats to vehicles and protect them from cyberattacks.” In other words, a management system structures your company's approach to safety and security. Your employees can concentrate on the various tasks at hand. With the management system, they bring these tasks together and operate the interfaces.
Aspects of a management system include:
- The cybersecurity culture.
- The organizational structure.
- The documentation of the required development processes and procedures.
- Monitoring whether this work results in appropriately secure products.
- The necessary infrastructure.
- The required skills and competencies.
Don’t forget: A management system needs to follow a PDCA process: Plan > Do > Check > Act. The processes should be regularly evaluated for effectiveness and efficiency. This includes audits by independent inspection bodies.
To summarize, a management system is about structures, processes, measures and competencies.
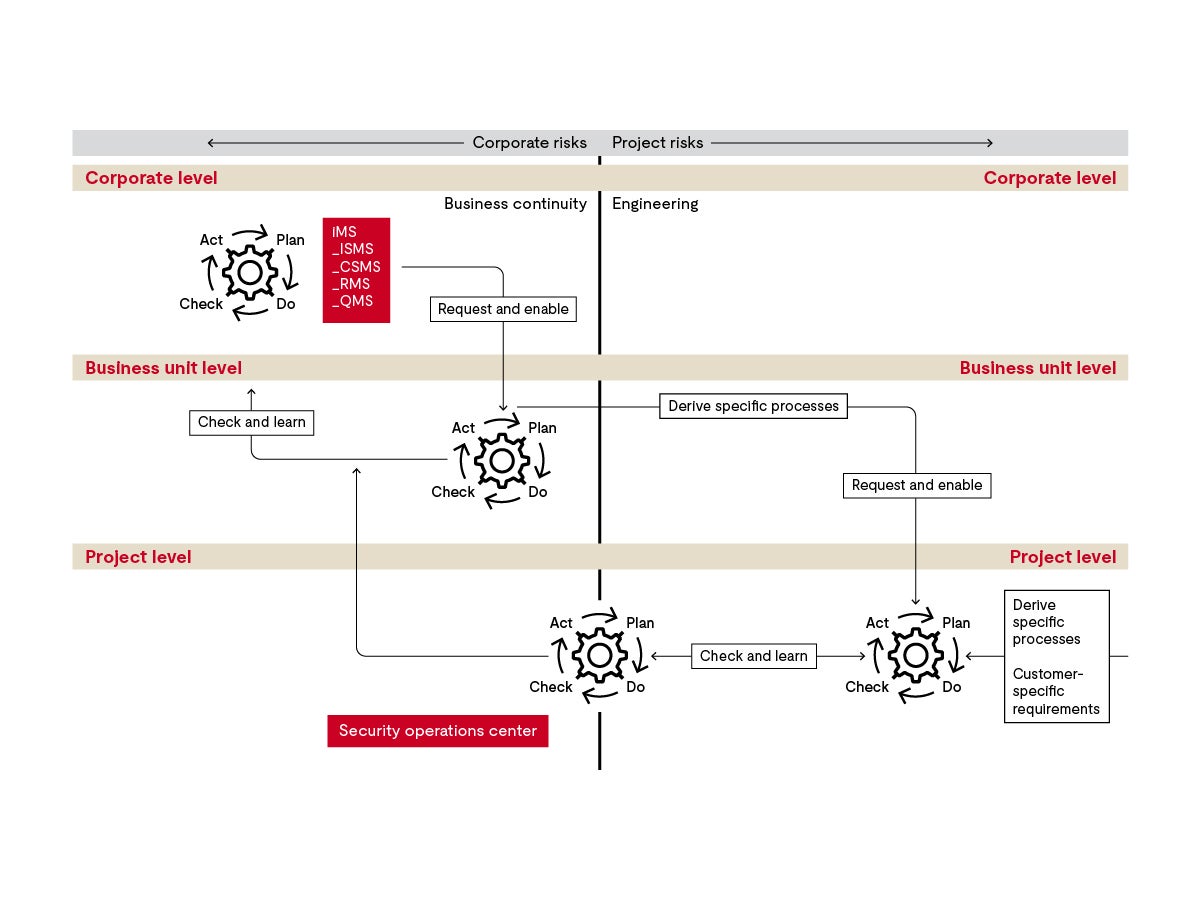
Let’s look at a blueprint of an integrated management system. There are three levels of concern, from the corporate level to the business unit to the projects.

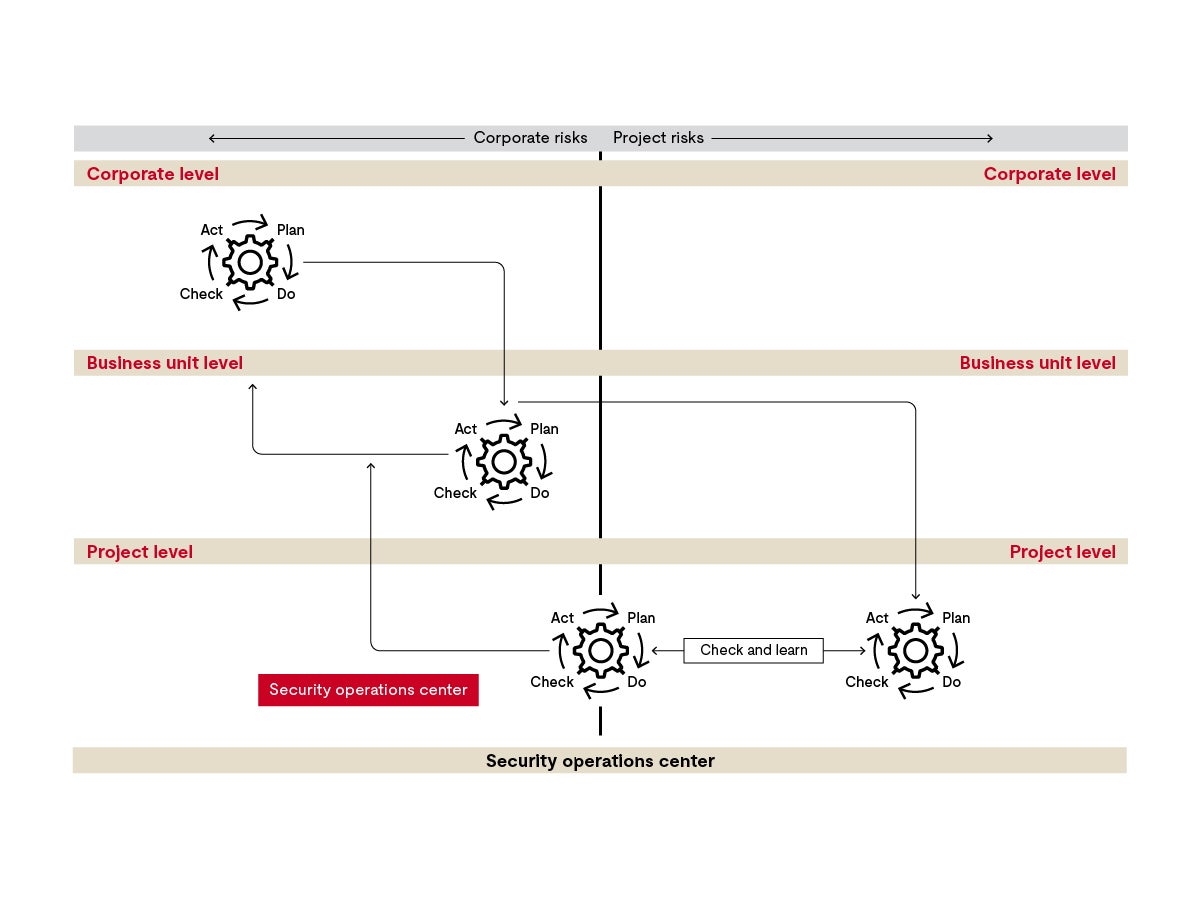
Corporate level
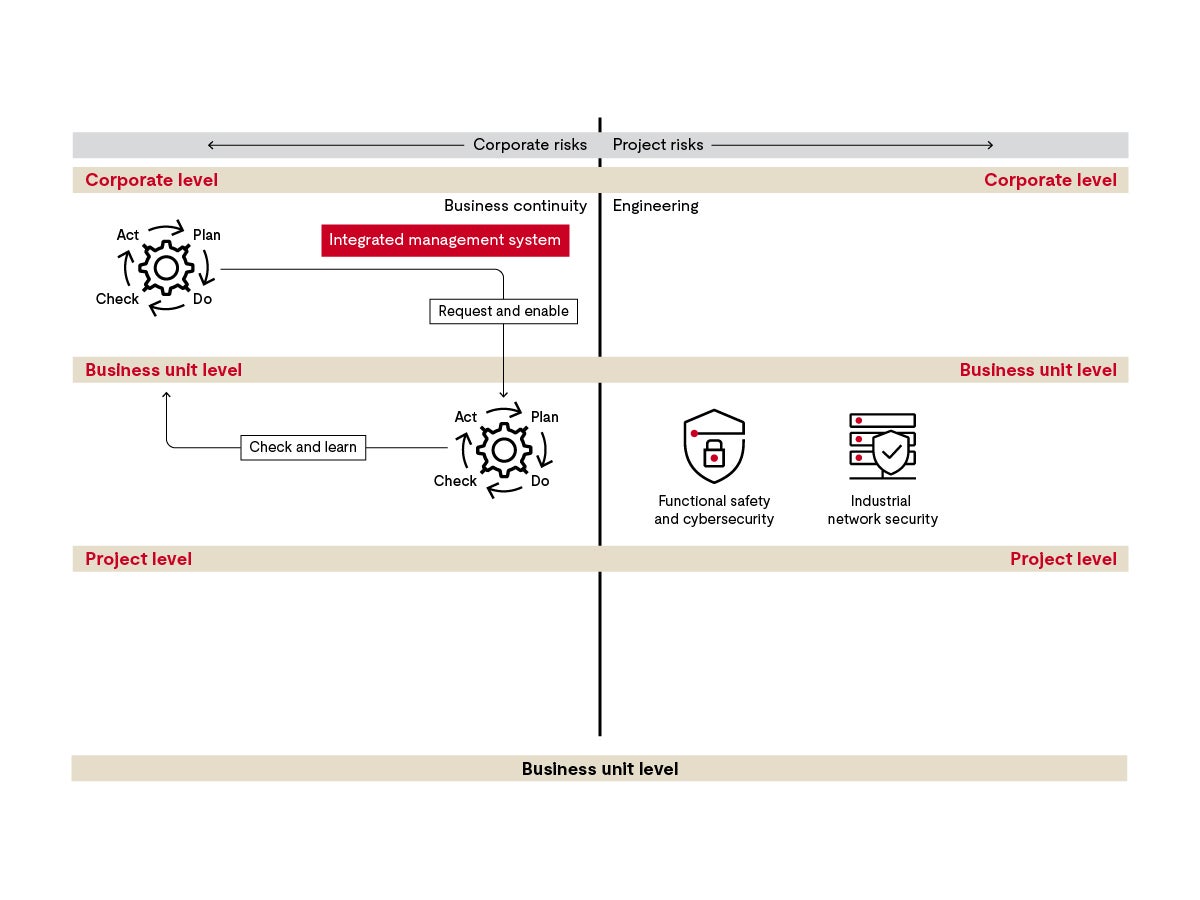
From the corporate perspective, the risks are different from those at the shop floor level, for example. The enterprise is interested in business continuity, while the projects must deal with the implementation of engineering solutions. The level of detail in a management system relates to the types of risks. The subsystem governs the appropriate way to deal with the latter. The dashed line in the middle also serves this distinction: it separates the business risks from the risks in your projects.
Now, we’ve implemented the leading management system on the corporate level. In our sample company, a car manufacturer, imagine a development of electronic systems and car production, so the management has to integrate requirements from a set of international standards. If you work for a company with multiple product lines, there may be additional requirements, such as off-highway vehicles.
Business unit level
Let's now switch to the business unit level. Here you need a mediation function. The system here should:
- Meet the requirements of the higher-level system.
- Enable the downstream systems at the project level.
If this business unit is a research and development unit, you can focus on the requirements of functional safety and cybersecurity, while the industrial networks requirements in the plant are the responsibility of a management system in another business unit.
On the left you can see the feedback loop: measures that ensure learning and improvement are an integral part of the management systems.
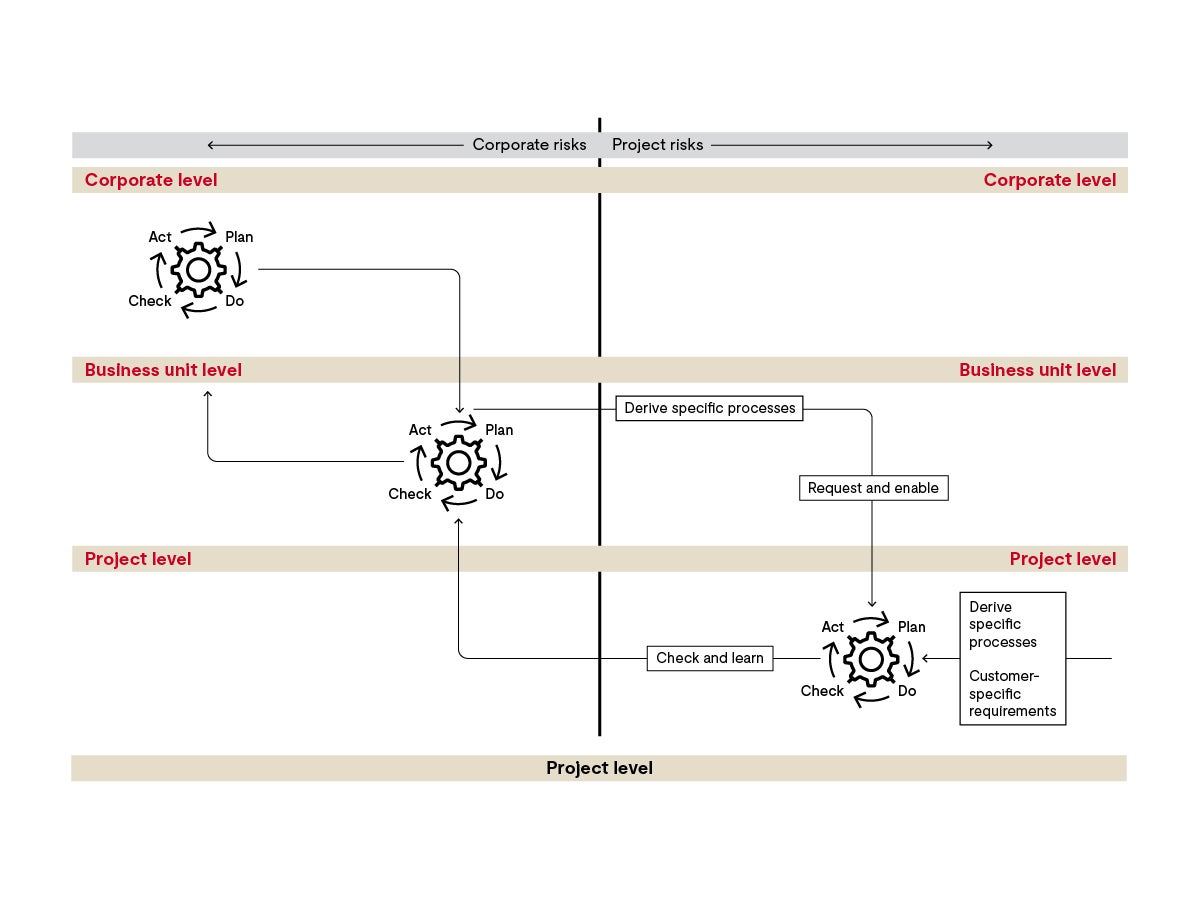
Project level
When we approach the project level, we also cross the threshold from company-related to project-related risks. Derive specific processes to guide the implementation of cybersecurity measures for use in the field. For example, when must the project lead conduct risk assessments?
As the project lead, you are also confronted with requirements from third parties, especially from your customers. Therefore, you also need to know how you can cope with additional customer specifications, some of which go beyond those of your standards.
As you can see, an integrated management system addresses cybersecurity concerns at the appropriate levels. There, you should derive corresponding sub-systems with structures, processes, measures and competencies.
Security operations center
There’s is one more concern: Continuous monitoring of the cybersecurity posture. You learned about this in the first video. The function of a cybersecurity operations center is also linked to your management system.
A security operations center performs continuous field monitoring. To do this, they scan external sources for information and see if they can find evidence of potential vulnerabilities. They even hold bug bounty parties to unearth possible vulnerabilities. Analytical and forensic teams operate in the security operations center. They use penetration tests to check whether their own system is vulnerable. They make triage decisions and assess events on whether a potential vulnerability can harm in-house systems. Vulnerability management teams work with development teams on affected projects; if the system is already compromised, cybersecurity emergency response teams investigate what countermeasure is appropriate. You can also design this unit as a center of excellence for cybersecurity. Then the unit acts as a powerhouse, supporting developers in the field with training and in-depth expertise.
Conclusion
In short: With your CSMS in place, you ensure that all necessary cybersecurity activities for
- Development
- Production
- Post-production
are carried out thoroughly and until the vehicle series finally reaches the end of its support. With the inclusion of the CSMS in your integrated management system, you ensure all necessary cybersecurity and complementary activities are synchronized. This starts at the enterprise level in terms of business risks and continues throughout the product lifecycle, from the concept phase through development to production and the end of operations.
Implement the management system carefully to foster and establish a cybersecurity culture in your corporation, and cybersecurity concerns will become second nature to you and your colleagues.
Cybersecurity is not an afterthought!
Want to learn more about automotive cybersecurity? Explore our trainings.
About the author
Thomas Liedtke is a computer scientist by background. After completing his PhD at the University of Stuttgart, he entered the telecommunications industry. Over the course of 14 years at Alcatel-Lucent, he successfully spearheaded a variety of projects and managed several departments. He entered the field of consulting over a decade ago and has been sharing his experience with clients in a variety of industries ever since, primarily in the areas of safety, security, privacy and project management.
He has been involved with several committees, particularly the working group for Automotive Cybersecurity at German Electrical and the VDA Cybersecurity Work Group organized by the (DIN standard NA052-00-32-11AK and ISO standard TC22/SC32/WG11).
