There is no single comprehensive cybersecurity standard that suits every automotive application. Instead, there are scores of regulations, standards and manuals that cover individual aspects or phases of the product development process and the vehicle life cycle. This volume of standards and corresponding approaches reflects the large number of automotive cybersecurity requirements, including cybersecurity in vehicle development, secure production processes, secure fleet operations, and the protection of backend systems and data.
Automotive cybersecurity activities do not end after a product is developed or when a vehicle enters or is taken off the market. Cybersecurity activities can only be stopped when the last vehicle has been scrapped at the end of the period of use guaranteed by the manufacturer in keeping with data protection requirements, during which reading private keys was made impossible. The development organization must understand how long the manufacturer will provide support in the future.
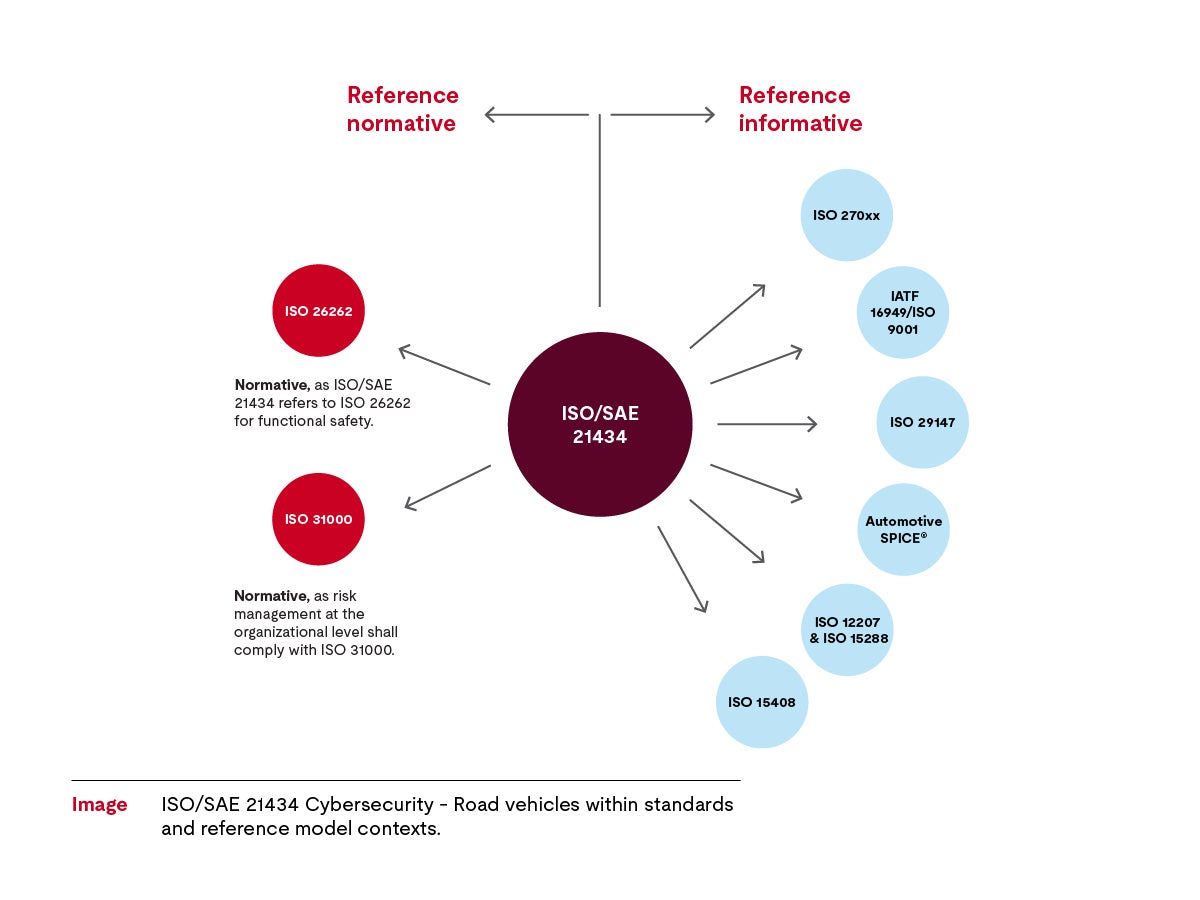
ISO/SAE 21434
Amid the backdrop of this automotive cybersecurity regulatory landscape, the publishing of United Nations Economic Commission for Europe (UNECE) regulations and ISO/SAE 21434 set automotive cybersecurity requirements that vehicle manufacturers and automotive software developers must meet in order for connected vehicles to be approved for sale and distribution.
ISO/SAE 21434, Road Vehicles — Cybersecurity Engineering, incorporates cybersecurity engineering within the automotive electronic product development process. The standard defines technique and cybersecurity requirements that engineers are expected to adhere to in their work. ISO/SAE 21434 offers an understanding of the current status of product development. It explains where automotive electronics companies must start and covers processes from planning and defining specifications to implementation, verification and testing.
Unlike ISO 26262, Road Vehicles — Functional Safety, ISO/SAE 21434 is abstract and meets the diverse interests and expectations of multiple countries. ISO/SAE 21434 creates a common language and shared understanding of what cybersecurity entails for the automotive industry to better facilitate manufacturers’ and suppliers’ alignment of cybersecurity activities.
For example, ISO/SAE 21434 does not name specific technical requirements for hardware metrics or architecture specifications. Because cybersecurity concepts quickly become obsolete, approaching security from multiple angles makes it more difficult for threat actors to exploit vulnerabilities. The standard states what is to be done but not how it is to be achieved.
Although the standard itself is concise, its comprehensive annexes offer best practices, examples and blueprints for its application.
ISO/SAE 21434 introduces new challenges for automotive manufacturers and developers
ISO/SAE 21434 requires automotive manufacturers to prove they have a cybersecurity management system of the appropriate breadth and depth in place within their organization and demonstrate that all cybersecurity activities are planned and executed according to the required procedures. These measures help the organization avert new vulnerabilities and meet cybersecurity objectives.
In light of these requirements, cybersecurity, quality and business management teams face the challenge of developing a cybersecurity management system that matches the current state of technique and offers the required practical robustness without having guidelines for development process standards or information about tools, secure code or security by design.
These challenges begin with defining individual roles, capturing corresponding responsibilities and integrating these into organizational structures and workflows. Although existing departments such as quality assurance, functional safety and IT security may carry many of these responsibilities, organizations may need to form new departments because existing roles may not possess the required capabilities.
For example, a continually active analysis center, which organizations often lack, must observe cybersecurity attacks independent of specific projects. The analysis center would also produce reports on vulnerabilities, develop routines, determine how intrusion scenarios are dealt with, run a 24/7 hotline and manage the available tools. This vehicle cybersecurity operations center must have an up-to-the-minute understanding of key issues as well as access to crucial information in the event of an occurrence.
Threat analysis and risk assessment
A key component of ISO/SAE 21434 is the threat analysis and risk assessment (TARA). This analysis and evaluation instrument for damage scenarios, threat scenarios and attack feasibility that determines risk during the concept phase.
Addressing ISO/SAE 21434 requirements
To meet cybersecurity requirements established in ISO/SAE 21434, automotive manufacturers must be able to:
-
Show and document that your assessments address all issues and that derived security goals are adequate and effective.
-
Demonstrate that defined cybersecurity goals have actually been achieved.
-
Apply expertise gathered through previous projects and processes across the organization.
View the infographic below to further your understanding of ISO/SAE 21434 in the context of other standards and reference models.

UNECE regulations impacting automotive cybersecurity activities
At nearly the same time as ISO published ISO 21434, the United Nations Economic Commission for Europe (UNECE) published new regulation guidelines for vehicle type approvals. In June 2020, UNECE Working Party 29 adopted two regulations — UN R155 and R156 — that significantly impact homologation in other areas of the automotive industry. Unlike ISO standards, these regulations have a legal impact via national or European legislation. Under these guidelines, vehicles cannot be brought to market without certification under these guidelines.
In the European Union, UN R155 and UN R156 are formulated and scheduled as the General Safety Regulation.
UN R155
UN R155 requires manufacturers to take responsibility for the overall cybersecurity of their automotive systems. ISO/SAE 21434 provides a foundation to meet the requirements of UN R155, as it requires manufacturers to establish a cybersecurity management system (CSMS) spanning different projects, including building capabilities to analyze potential cyberthreats.
According to UN R155, an independent certification authority must assess and validate whether the CSMS adheres to requirements and is integrated into project activities so that the required cybersecurity tasks are carried out on an ongoing basis. Certification is valid for three years and must be submitted to national authorities.
UN R156
UN 156 considers the importance of updates — whether over the air or via charging stations — are critical to connected vehicles’ security over the entirety of their lifetime. For compliance with UN R156, manufacturers must establish a software update management system (SUMS) that meets certification requirements. The SUMS must give each homologation-relevant software system a unique identification number (RXSWIN) and track which versions have been installed in vehicles. Certification for all RXSWINs must be submitted when applying for approvals. ISO 24089, Road Vehicles — Software Update Engineering, proposes fundamentals for a SUMS and thus plays a role in the development of a SUMS.
Both UN R155 and R156 also define requirements for national processes governing vehicle approvals because the independent auditing of management systems and the certification of automotive critical systems must be laid down and checked by supervisory authorities.
Get connected with our team
Thanks for your interest in our products and services. Let's collect some information so we can connect you with the right person.
