Vehicle manufacturers must protect their products against cyberattacks during the entire lifetime of the connected car to mitigate safety, financial, operational and privacy risks. At the center of automotive cybersecurity is the threat analysis and risk assessment (TARA), a comprehensive risk assessment procedure to be executed during the concept phase. ISO/SAE 21434 outlines the basic elements of a risk assessment for road vehicles.
Manufacturers cannot foresee the motivations or the abilities of threat actors in the future. Despite this, manufacturers must work to understand where and how their products are vulnerable, what harm is associated with each threat, and how they intend to manage the impact of the threats.
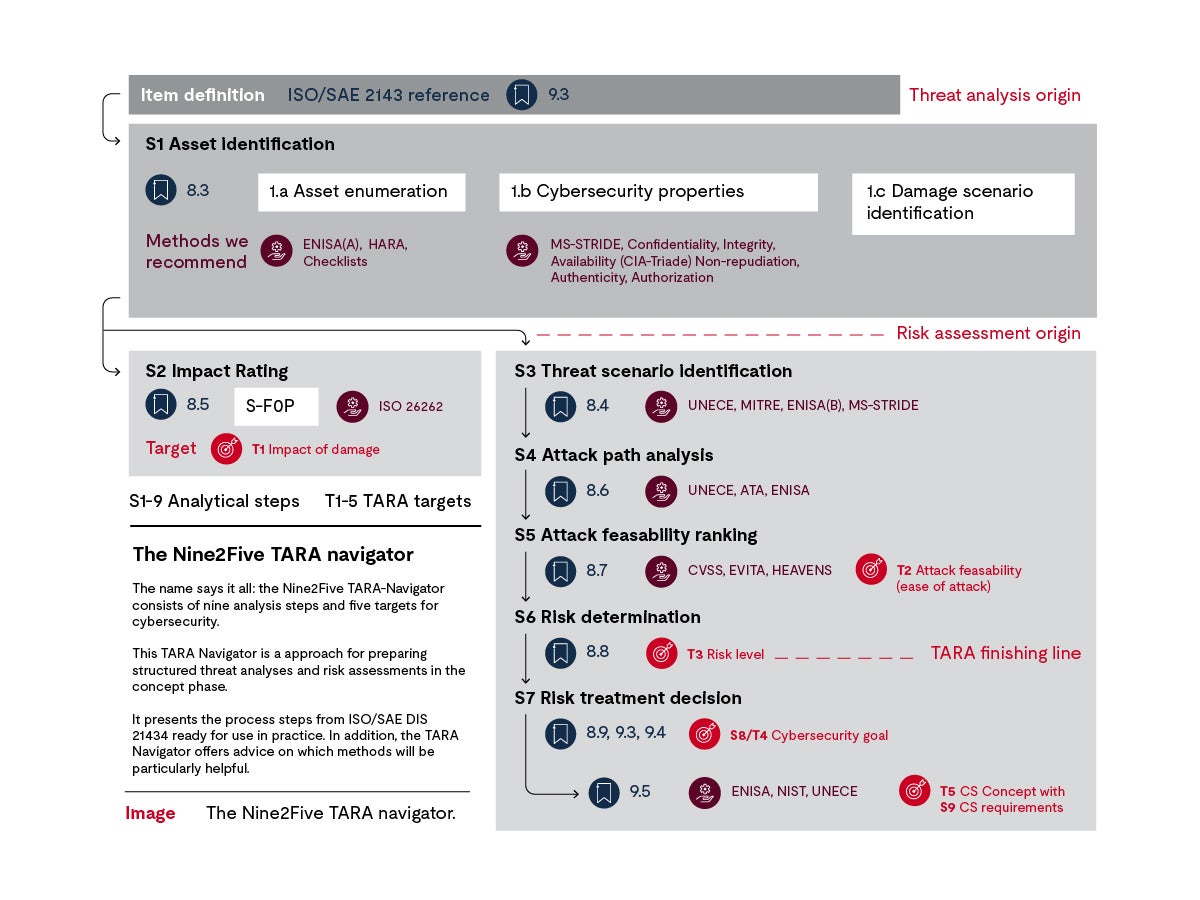
In a TARA, items are checked and related to each other in a sequential, structured process encompassing nine steps and five targets.
Nine steps and five targets to navigating a TARA
Before you begin a TARA
Before you can start a TARA, you first must define your item. Is it a subsystem or a set of subsystems, a vehicle-level function or a control unit? Describe the system’s environment, functions, interactions and interfaces.
- Step 1: Asset identification
An asset is something related to the item that is crucial for a stakeholder and worth protecting. Examples of assets include internet communication channels, encryption keys and safety goals. The asset is important not only to the stakeholder — who benefits from its functionality — but also to a threat actor — who can use it to compromise the system.
Therefore, the first task is to list all your assets. Then systematically ascertain the following cybersecurity attributes of question each asset:
- Confidentiality
- Integrity
- Availability
- Nonrepudiation
- Authenticity
- Authorization
Next, identify the damage scenarios by evaluating what could happen if the assets’ cybersecurity properties are compromised.
- Step 2: Impact rating
In this step, we evaluate the damage scenarios according to what consequences they may have for your stakeholders. This includes functional safety, finance, operations and privacy. ISO 21434 provides guidance on how to determine the damage scenario's severity. We can provide formulas and preset templates to help you calculate the ISO 21434 severity determination. A damage scenario will not impact each stakeholder equally.
This also accomplishes Target 1: rating the impact of damage.
- Step 3: Threat scenario
In this step, we look at the assets again and determine what threat scenario may arise. A threat scenario is one potential way in which a damage scenario could be realized. In the threat scenario analysis, we try to identify what could happen if an item for which a security property of an asset is violated, and a threat scenario is realized. There are multiple ways to determine a damage scenario. For example, if we consider a compromised switch, the damage scenario could result in a possible threat scenario, namely by spoofing or flooding the controller area network (CAN) bus.
- Step 4: Attack path analysis
Next, consider what path a potential attacker must follow for the threat scenario to occur. This is called attack path. For example, the compromised switch we considered in the previous step is located somewhere in the middle of the vehicle. To compromise the CAN bus, an attacker has to find a way through the system. The aim of this step is to identify this path.
ISO/SAE 21434 ignores the intruder and the possible motivation. Instead, it focuses on the technical possibility of an attack, reverse-engineering how an attack on a compromised cybersecurity property would have to be configured to be successful.
The United Nations Economic Commission for Europe (UNECE) regulations UN R155 and R156 provide a list of examples of vulnerabilities. Determine if these vulnerabilities are relevant in your system and identify additional threat scenarios.
- Step 5: Attack feasibility rating
Not every theoretically possible attack is feasible in practice. Encryption, for example, may make a possible attack unlikely. In this step, we evaluate the potential for the attack to take place by considering five key parameters:
- Elapsed time
- Required expertise
- Product know-how
- Required equipment
- Window of opportunity
Once we determine whether it is feasible for an attacker to conduct a successful attack, we have achieved Target 2: rating the feasibility of an attack (also called ease of attack).
- Step 6: Risk value determination
In this step, we combine the results of the impact rating (the impact of the associated damage scenario, Target 1) and attack feasibility rating (the feasibility of the attack paths, Target 2):
Risk value = Impact × Attack feasibility
Because stakeholders may assess risks differently, we must apply a different risk value for each stakeholder.
This step achieves Target 3: determining the risk value.
- Step 7: Risk treatment decision
Manufacturers have several options for dealing with risks:
- Avoidance
- Reduction
- Sharing or transferring to third parties
- Acceptance
A proper method of risk reduction is the specification of a security control (technical or organizational) or the introduction of redundancy. Third parties interested in risk transfers are insurance companies. Decide how you want to manage the risk.
It can be challenging to determine the effectiveness of a cybersecurity control, but this is a key activity in risk assessment.
- Step 8: Cybersecurity goals
The cybersecurity goals and claims are derived from the results of the TARA and your decisions about how the risks should be dealt with. If you decide that you want to avoid a risk, then you may consider an alternative technical solution.
The cybersecurity goals form Target 4 of the TARA.
- Step 9: Cybersecurity concept
The cybersecurity concept is derived from the cybersecurity goals and describes how to put the cybersecurity goals in practice. Derive requirements from the goals and allocate them to your architecture — the relevant components of your systems and organization. The cybersecurity concept includes these requirements and their allocation to the architecture.
The cybersecurity concepts achieve Target 5: capture all cybersecurity requirements and their allocation.
These are the essential steps for performing a TARA according to ISO/SAE 21434 requirements. This standard expects manufacturers to perform a TARA on a regular basis.

UL Solutions Software Intensive Systems experts can support you in:
- Fostering awareness for the need for comprehensive end-to-end safeguards.
- Detailed assessments of any threats posed.
- Matching your cybersecurity policies to processes, products and IT requirements and managing involved specialists.
- Assessing and improving your development processes with respect to security issues.
- Adapting existing workflows and procedures to address key cybersecurity issues.
- Ensuring systems conform to UNECE homologation guidelines.
- Defining and introducing new development processes that comply with the requirements of ISO/SAE 21434.
- Evaluating, developing and implementing cybersecurity management systems.
- Selecting of relevant security technology and industry standards according to your requirements.
We also offer templates and kits for ISO work products.
Get connected with our team
Thanks for your interest in our products and services. Let's collect some information so we can connect you with the right person.
