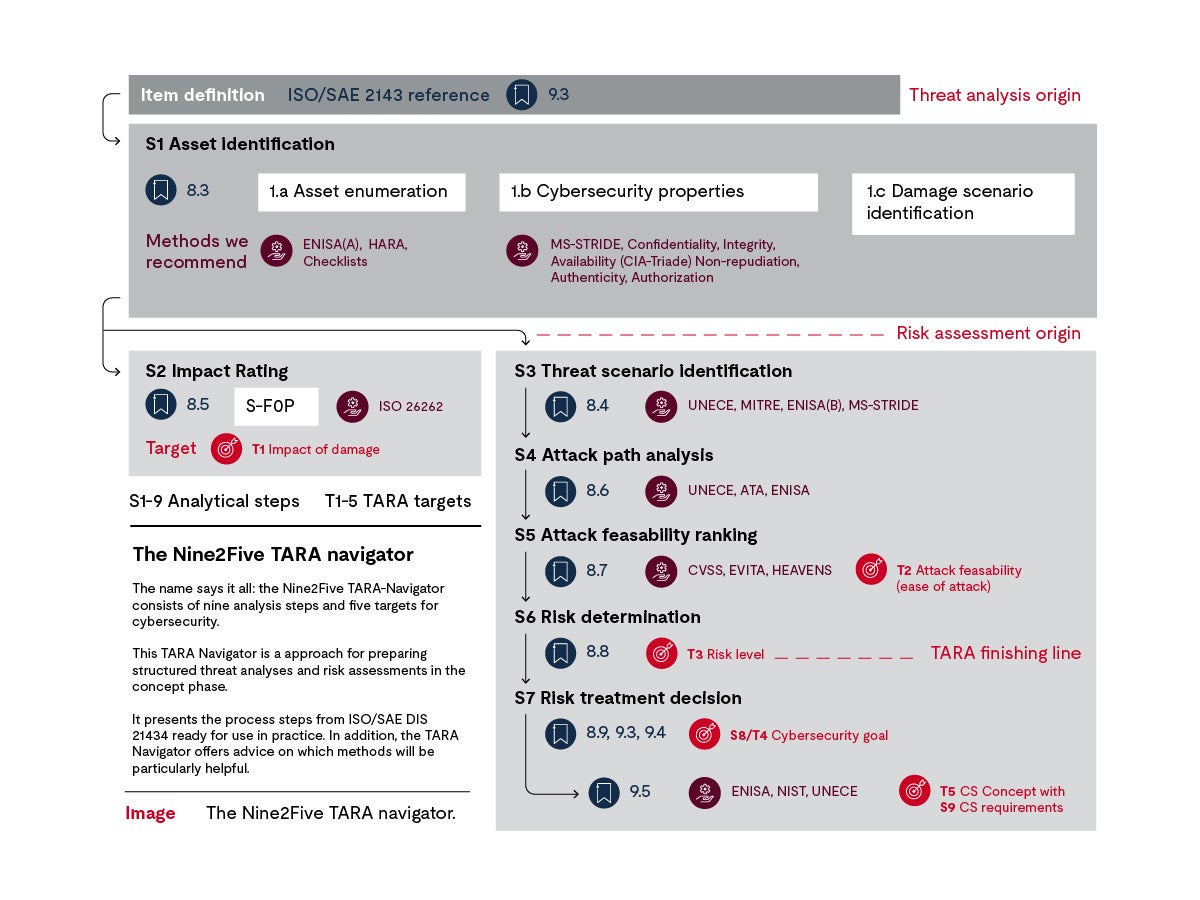
The TARA Navigator

It prepares the process steps from ISO/SAE DIS 21434 for use in practice. In addition, the TARA Navigator provides you with information on which methods are particularly helpful.
Risk assessments are the centerpiece of automotive cybersecurity. Therefore, Clause 8 of the coming ISO/SAE 21434 industry standard outlines the basic elements of a risk analysis. In the concept phase, a comprehensive risk assessment is expected: the TARA.
The TARA Navigator is a practice-proofed approach to performing risk analysis in a smart and structured manner.
The connected car and its components must be safe and secure during its entire lifetime. For this, you must protect your products against cyberattacks. Otherwise, your stakeholders will suffer losses in terms of safety, finance, operations or privacy.
ISO/SAE 21434, Road vehicles – Cybersecurity engineering
But do you really know all the potential threat scenarios that your vehicle project will be exposed to? You cannot foresee the motivation or the abilities of a future attacker. To cope with this challenge, you must continuously find out:
- If your product is vulnerable.
- What harm is associated with the threat.
- How you intend to manage the impact of the threats.
A risk analysis is a procedure in which findings are checked and related to each other in a structured, step-by-step manner.
The nine steps of the TARA Navigator are aimed at five targets:
- Impact of damage
- Attack feasibility
- Risk value
- Cybersecurity goals
- Cybersecurity concept
Item definition
Before you can start with your TARA, you must define your item first. This is a sub-system or a set of sub-systems (for example, a function or a control unit). Describe the environment of this system: its functions, interactions and what interfaces there are.
Steps 1 and 2 address Target 1: impact of damage.
Step 1: Asset identification
An asset belongs to your item, and it is worth protecting. It defines a property crucial for functionality. Take, for example, the internet communication channel — hardly any electronic system is conceivable without this asset. Encryption keys or safety goals are further examples.
However, the asset is very interesting for two parties: your stakeholder who benefits from its function, and an attacker who plans to compromise your system.
Therefore, the primary step is to enumerate all your assets.
What can go wrong?
Systematically question each of the assets in terms of
- Confidentiality
- Integrity
- Availability
as well as
- Non-repudiation
- Authenticity
- Authorization
The ISO/SAE 21434 standard describes these attributes as cybersecurity properties.
You identify a damage scenario by checking what happens if one of the cybersecurity properties is compromised.
Step 2: Impact rating
Here we evaluate the damage scenarios according to what consequences they may have for your stakeholders. This includes functional safety, finance, operations and privacy. Tables help to determine the damage effect. The catch here is that not every stakeholder is equally affected by every damage scenario.
We have now achieved our first target: We’ve rated the impact of damage.
Steps 3, 4 and 5 address Target 2: attack feasibility.
Step 3: Threat scenario identification
In the first step, we spoke about the potential damage caused by a compromised cybersecurity property. Now we look at the selected assets again and ask what threat scenario may arise.
For example. consider a defective switch. This damage scenario results in a possible threat scenario, namely the compromising of the CAN bus by spoofing or flooding.
Step 4: Attack path identification
Imagine that this defective switch is somewhere in the middle of the vehicle. To compromise the CAN bus, an attacker must find a way through the system. The ISO standard now thinks backwards: What path must a potential attacker follow for the threat scenario to occur? The theoretical path is called an “attack path.”
You’ll find a list of samples of vulnerabilities in UNECE regulations. See if any of these vulnerabilities are present in your system.
Theory is fine. But is this attack realistic?
Step 5: Attack feasibility rating
In practice, not every attack can be conducted. For example, a potential attack path may be highly unlikely due to encryption. Therefore, we now look at the actual attack potential. There are five key parameters for your evaluation:
- Elapsed time
- Required expertise
- Product know-how
- Equipment
- Window of opportunity
Once we know whether an attacker can conduct an attack successfully, we have achieved target number two: Rating of the feasibility of an attack.
Step 6 addresses Target 3: risk value.
Step 6: Risk value determination
For this step, we combine the results of both targets: impact rating (target 1) and attack feasibility rating (target 2).
ValueRisk = ImpactDamage x FeasibilityAttack
We therefore have two ratings that determine the risk value:
- The impact of the associated damage scenario.
- The attack feasibility of the attack paths.
However, different stakeholders may assess the risks very differently. That makes things tricky; we may have to apply a different risk value for each stakeholder. In any case, we have achieved the third target: we know the risk value.
Steps 7 and 8 address Target 4: cybersecurity goals.
Step 7: Risk treatment decision
Once the risks are revealed, the question is how to deal with them. There are a set of options for dealing with risks:
- Avoidance
- Reduction
- Sharing or transfer to third parties
- Acceptance
Risk reduction may involve introducing redundancy or placing a security control on technical or organizational levels. Risk sharing may involve distributing the negative impact of a potential risk across multiple parties.
Now decide how you want to manage the risk.
Please keep in mind: It is very tricky to judge how effective a cybersecurity control is. However, this is where every risk assessment stands and falls.
Step 8: Cybersecurity goals
The cybersecurity goals and claims are derived from:
- The results of the TARA.
- Your decisions on how the risks should ultimately be dealt with.
If you decide that you want to avoid a risk, then you go back to the beginning. Or you may consider an alternative technical solution.
The cybersecurity goals form the fourth target of the TARA.
Step 9 addresses Target 5: cybersecurity concepts.
Step 9: Cybersecurity concept
The cybersecurity concept is derived from the cybersecurity goals. It describes how you want to put the cybersecurity goals in practice. Derive requirements from the goals and allocate them to your “architecture”: the relevant components of your systems or organization.
These requirements and their allocation to the architecture are all described in the cybersecurity concept.
The cybersecurity concepts capture all cybersecurity requirements and their allocation, this is our last target: cybersecurity concepts.
There you have it: The TARA Navigator, comprised of nine steps addressing five targets. Each step builds on the step that came before it.
About the author
Thomas Liedtke is a computer scientist by background. After completing his PhD at the University of Stuttgart, he entered the telecommunications industry. Over the course of 14 years at Alcatel-Lucent, he successfully spearheaded a variety of projects and managed several departments. He entered the field of consulting over a decade ago and has been sharing his experience with clients in a variety of industries ever since, primarily in the areas of safety, security, privacy and project management.
He has been involved with several committees, particularly the working group for Automotive Cybersecurity at German Electrical and the VDA Cybersecurity Work Group.
